Executive Summary
This report details Lazarus Group Bitcoin Mixing activities and the findings of our recent monitoring and analysis of mixing and laundering activities, specifically focusing on their utilization of Bitcoin mixing services. Our investigation has identified a coordinator, “Kruw,” as a key facilitator in the mixing of potentially stolen funds and Lazarus Group Bitcoin laundering efforts, including those originating from Bybit. Kruw operates using infrastructure based on Wasabi’s open-source code. This report provides evidence of Lazarus Group Bitcoin mixing involvement in mixing rounds facilitated by Kruw and includes a sample transaction for illustrative purposes. Further analysis of the collected data provides a deeper understanding of the Lazarus Group’s operational methods.
1. Introduction:
Over the past few weeks, we have been actively monitoring and collecting data on various Bitcoin Mixing coordinators. This ongoing effort aims to identify and track entities involved in potentially illicit financial activities within the cryptocurrency ecosystem. This report presents our findings regarding the Lazarus Group’s use of a specific Coinjoin coordinator, “Kruw,” for the purpose of obfuscating the origin of their Bitcoin holdings.
2. Identification of the Coordinator: Kruw
Our monitoring has led to the identification of a Bitcoin mixing coordinator operating under the name “Kruw.” Our analysis of the coordinator’s rounds strongly suggests its utilization by the Lazarus Group for the mixing of stolen funds. Notably, Kruw employs the open-source code of Wasabi Wallet as the underlying infrastructure for its operations. It is important to clarify that this coordinator is distinct from the official Wasabi Wallet coordinator, which ceased its operations in 2024.
3. Evidence Linking Lazarus Group to Kruw:
Through the analysis of numerous mixing rounds, we have observed patterns and transaction flows indicating the involvement of the Lazarus Group with the Kruw coordinator. Our findings suggest that Kruw is being used to mix funds, including those believed to be stolen from Bybit.
4. Sample Mixing Round Analysis:
The following provides a detailed analysis of a sample mixing round where Lazarus Group funds are observed to be participating. This example illustrates the characteristics and parameters of the mixing activity facilitated by Kruw.
{
"CoordinatorEndpoint": "https://coinjoin.kruw.io/",
"EstimatedCoordinatorEarningsSats": 17044,
"RoundId": "96843338e1f333467c2f5b57a792b498481fc2b6d8e057005afaf45ca61684e1",
"IsBlame": true,
"CoordinationFeeRate": 0,
"MinInputCount": 100,
"ParametersMiningFeeRate": 2,
"RoundStartTime": "2025-03-25T09:18:10+00:00",
"RoundEndTime": "2025-03-25T09:23:42+00:00",
"TxId": "4b298fd10887160d1125a6e37413bfec658c52d95737494a4fa04ab95afca812",
"FinalMiningFeeRate": 2.01,
"VirtualSize": 21887,
"TotalMiningFee": 44009,
"InputCount": 203,
"TotalInputAmount": 1341025782,
"FreshInputsEstimateBtc": 2.21198521,
"AverageStandardInputsAnonSet": 5.71,
"OutputCount": 239,
"TotalOutputAmount": 1340981773,
"ChangeOutputsAmountRatio": 0.0049,
"AverageStandardOutputsAnonSet": 9.08,
"TotalLeftovers": 17044
}
5. Visualization:
To further illustrate the flow of funds and the involvement of the Lazarus Group, we have prepared the following visual representations:
-
- Graph 1: A graph depicting the flow of funds from identified Lazarus Group Bitcoin addresses to a specific “hop” address. This visualization will clearly show the initial movement of potentially illicit funds.

-
- Graph 2: A graph illustrating the participation of the same funds (associated with Lazarus addresses) in a Coinjoin round facilitated by the Kruw coordinator. This will visually confirm their involvement in the mixing process. txid: 4b298fd10887160d1125a6e37413bfec658c52d95737494a4fa04ab95afca812
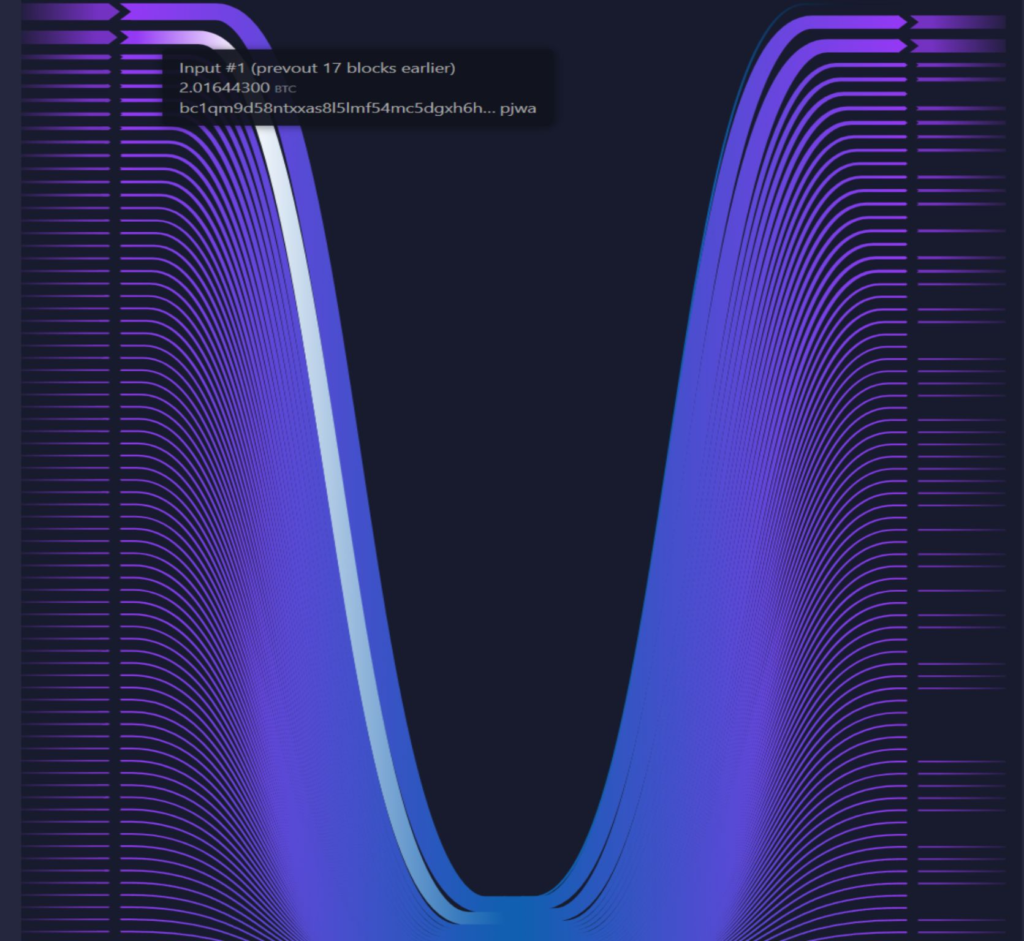
-
- Picture of Kruw’s Coordinator Profile: An image of the publicly available profile associated with the Kruw coordinator on X (Twitter) (or other relevant social media platform). This provides additional context.
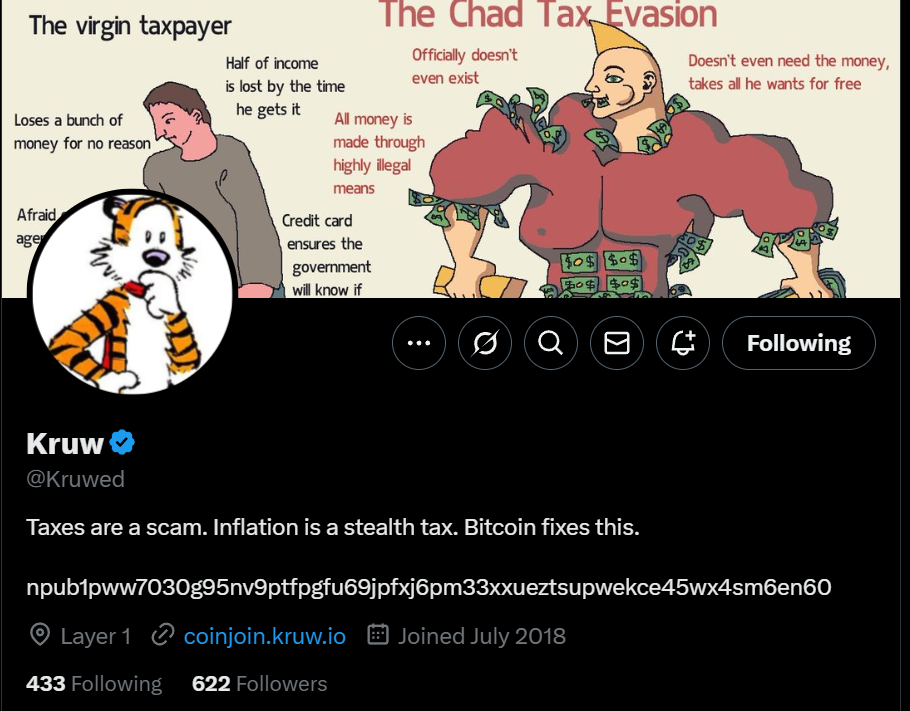
6. Conclusion:
Based on our monitoring and analysis, we have identified the Bitcoin mixing coordinator “Kruw” as a service provider utilized by the Lazarus Group for the purpose of obfuscating the origin of their Bitcoin holdings, including funds potentially stolen from Bybit. The provided sample transaction and accompanying visual evidence support this conclusion.
Read More of our Research
For further discussion or to access the complete dataset of mixing rounds analyzed, please do not hesitate to contact us at ziya@hexforensic.com
Disclaimer: This report is based on our analysis of publicly available blockchain data and other open-source information. The conclusions drawn are based on the available evidence at the time of this report and may be subject to further refinement as more data becomes available.
